Featured
this is a type of attack where the bad guys attempt to trick you into revealing personal information through text messages.
1 question this is a type of attack where the bad guys attempt to trick you into revealing personal information through text messages. One of the easiest ways for cybercriminals to find a target is through social media.
What Is Smishing Definition Examples Protection Tips Security Boulevard
At the moment there is a mystery shopping scam going on starting out with a text invitation asking you to send an email for more info which then gets you roped into the scam.

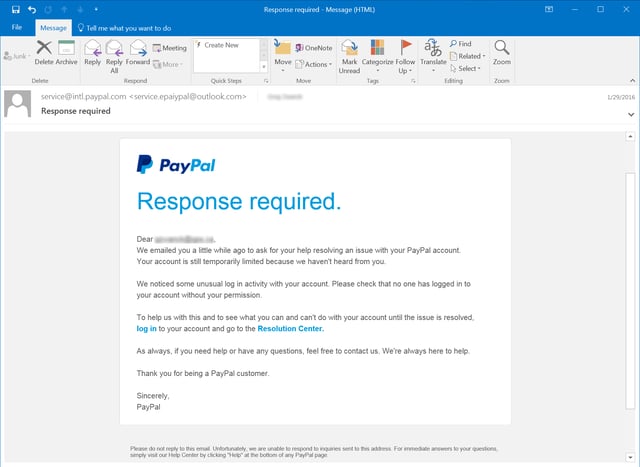
. In this ploy fraudsters impersonate a legitimate company to steal peoples personal data or login credentials. This is how the bad guys do it. Spear phishing attacks on social media often come from fake accounts but in a recent scam cybercriminals used real compromised accounts.
This is a type of attack where the bad guys attempt to trick you into revealing personal information through text messages. A worm is the form of malware that secretly gathers personal information about you. Those emails use threats and a sense of urgency to scare users into doing what the attackers want.
Pretexting An invented scenario is used to engage a potential victim to try and increase the chance that the victim will bite. However as technology continues to advance bad guys are always trying new methods to include tricking you with messaging technologies such as text messaging iMessageFacetime. False If you have a hardware firewall you shouldnt also use a software firewall.
Deceptive phishing is the most common type of phishing scam. Spear phishing is a phishing attack that targets a specific person and appears to come from a trusted source. Bad guys are increasingly targeting you through your smartphone.
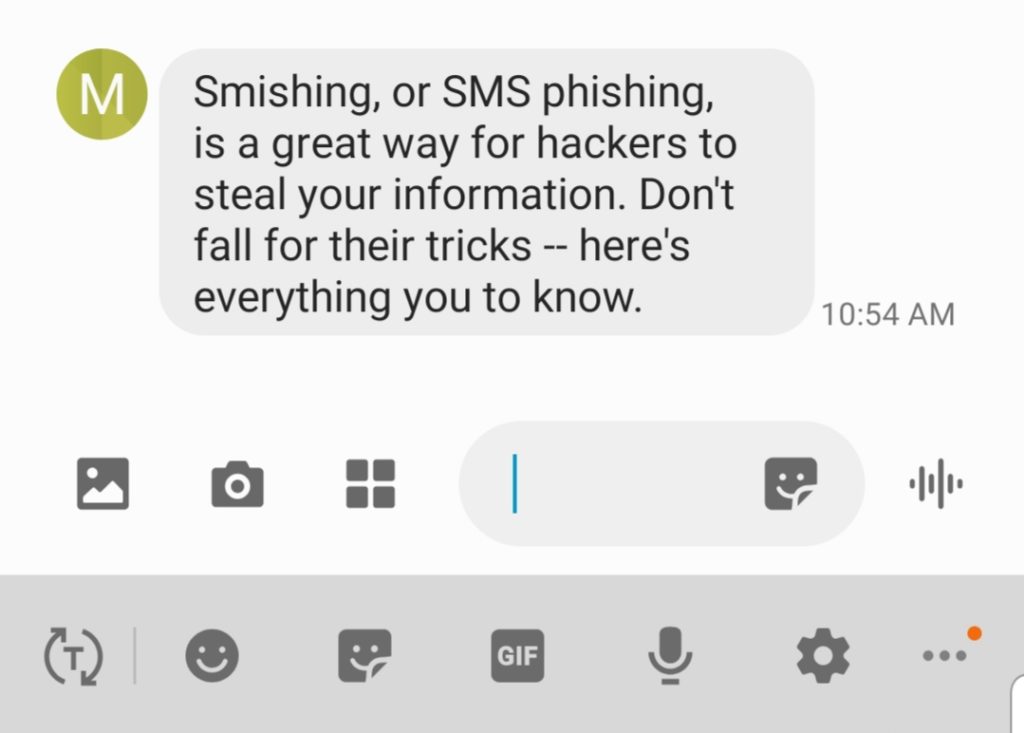
One of the most common ways cyber attackers attempt to trick or fool people is by scamming you in email attacks often called phishing or try to trick you with phone calls. SMiShing involves text messages sent to you in an attempt to get you to visit a link or send personal or confidential data to the sender. The text message may claim to be from your cell phone provider and request your payment information or may prompt you to click on a link and fill out a form to gain access to a prize.
Phishing attacks can also be done through a text message or phone call when the attackers pretend to work for popular companies such as Microsoft or Apple to trick users into revealing sensitive information. Attackers take the time to conduct research into targets and create messages that are personal and relevant. A smishing text for example attempts to entice a victim into revealing personal information via a link that leads to a phishing website.
Spear phishing is a very targeted type of phishing activity. Phishing is a type of social engineering where an attacker sends a fraudulent eg spoofed fake or otherwise deceptive message designed to trick a human victim into revealing sensitive information to the attacker or to deploy malicious software on. Incorporate threats fear and a sense of urgency in an attempt to manipulate the user into responding quickly.
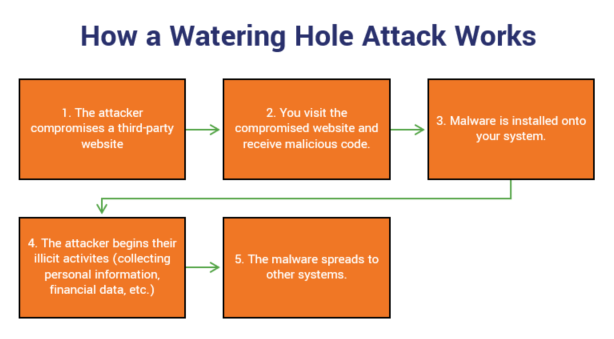
What is show in the above figure. A basic phishing attack attempts to trick a user into entering personal details or other confidential information and email is the most common method of. Quid pro quo Latin for something for something is a type of social engineering tactic in which the attacker attempts a trade of service for information.
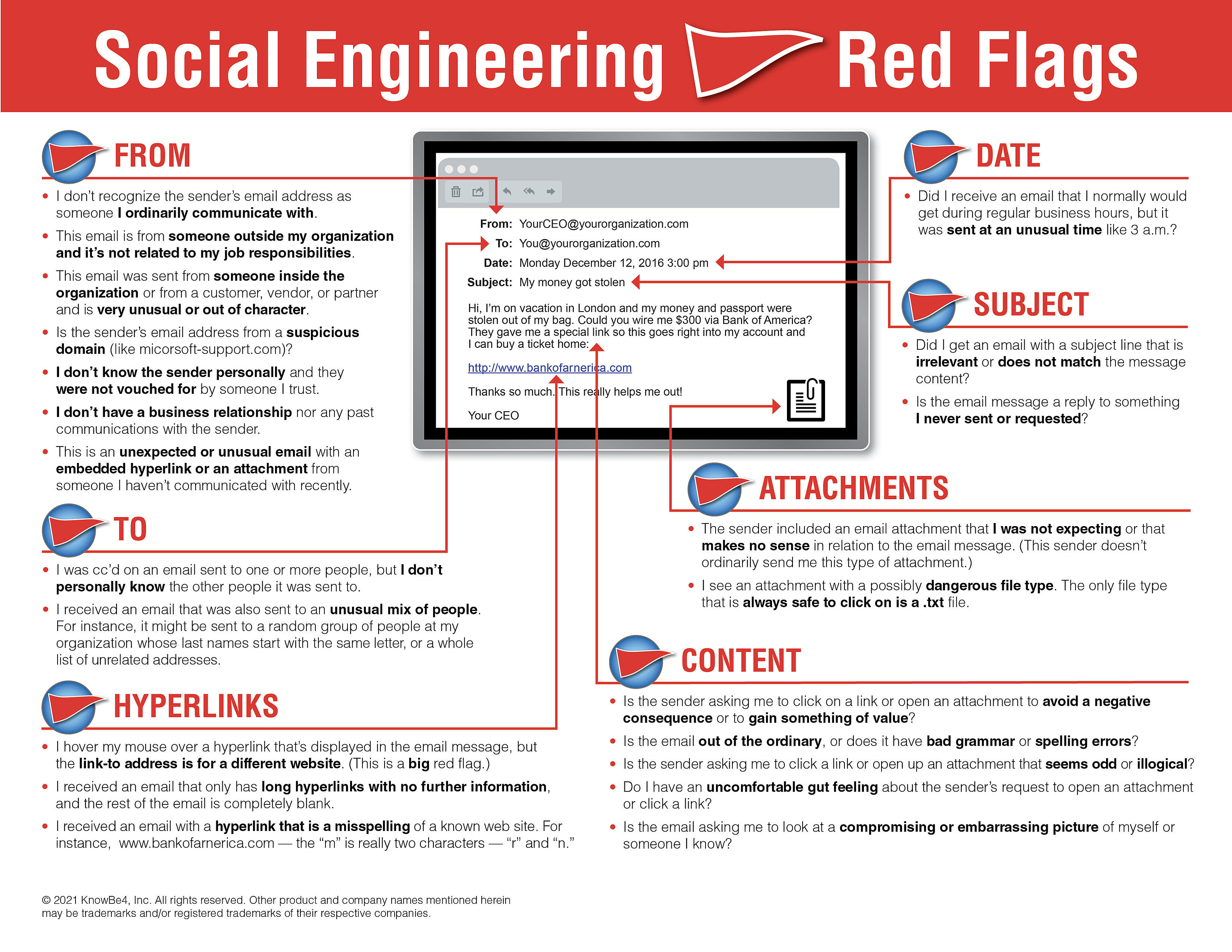
Social engineering is one of the most common and successful malicious techniques in. No two phishing emails are the same. Because of this spear phishing can be very hard to identify and even harder to defend against.
This is a type of attack where the bad guys attempt to trick you into revealing personal information through text messages. This type of attack has also been referred to as the Starbucks scam because it often takes place in coffee shops. A quid pro quo scenario could involve an attacker calling the main lines of companies pretending to be from the IT department attempting to reach someone who was having a technical issue.
Obtain personal information such as names addresses and Social Security Numbers. Its a false motive usually involving some real knowledge of the victim eg. Trojan A Trojan horse is a type of malware designed to mislead the user with an action that looks legitimate but actually allows unauthorized access to the user account to collect credentials through the local machine.
Smishing a portmanteau of phishing and SMS the latter being the protocol used by most phone text messaging services is a cyberattack that. They send texts that trick you into doing something against your own best interest. Use shortened or misleading links that redirect users to suspicious websites that host phishing landing pages.
False Security experts paid to find security holes in a system are called white hat hackers. Date of birth Social Security number etc in an attempt to get even more information. Evil twin phishing involves a cybercriminal creating a Wi-Fi hotspot that looks like the real one theyll even use the set service identifier SSID that is the same as the real network.
Social Engineering Attack is a type of attack that uses deception and trickery to convince unsuspecting users to provide sensitive data or to violate security guidelines. Techniques Used in Deceptive Phishing. This term refers to a social engineering technique where an unauthorized individual gains physical entry into a building or room by closely following behind someone who is authorized.
A phishing attempt performed using phone calls or by leaving voice messages is known as voice phishing or vishing. 1 on a question this is a type of attack where the bad guys attempt to trick you into revealing personal information through text messages.
What Is Smishing Definition Examples Protection Tips Hashed Out By The Ssl Store

6 Types Of Social Engineering Attacks

8 Types Of Phishing Attacks And How To Identify Them Cso Online

8 Types Of Phishing Attacks And How To Identify Them Cso Online
10 Types Of Phishing Attacks And Phishing Scams Hashed Out By The Ssl Store

8 Types Of Phishing Attacks And How To Identify Them Cso Online
Popular Posts
Animal Crossing Coffee Custom Design : How To Unlock Brewster S Rewards Animal Crossing New Horizons Wiki Guide Ign : I wanted a functional indoor/outdoor design with plenty of seating and bar space that incorporated all my favorite coffee shop features and .
- Get link
- Other Apps
Comments
Post a Comment